How to create and configure Extended Access Control Lists (ACL), access-list IOS command and access-group IOS command
Before continuing, refer Introduction to Access Control Lists lesson , if you are not familiar with Access Contol Lists.
Refer Extended Access Control Lists (ACL) lesson if you are not familiar with Extended Access Control configuration IOS commands.
You must be familiar with TCP port numbers for important services. Click the following link to learn important TCP port numbers.
Extended Access Control Lists (ACLs) - Lab Practice
The following diagram shows our Extended Access Control Lists (ACL) lab setup. We have three routers, three switches, six workstations and three servers connected as below. The host names, IP addresses and the interfaces of the routers are shown in diagram. The IP addresses of the workstations and the servers are also shown in the diagram.
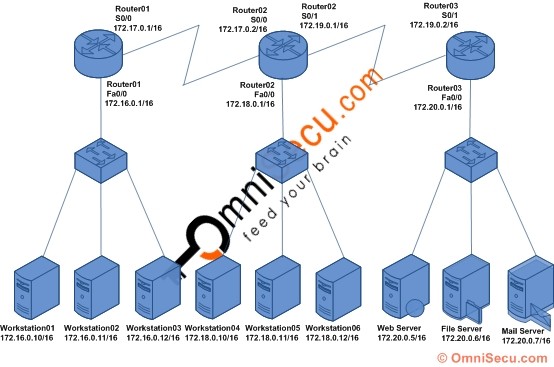
The purpose of this lab is to deny Workstation03 (IP address - 172.16.0.12/16) located at 172.16.0.0/16 network from accessing the Web Server (IP address - 172.20.0.5/16) at 172.20.0.0/16 network, using Extended Access Control Lists (ACL). Connect computers, switches and routers as shown in the figure. Configure the IP address and default gateway TCP/IP settings in all computers and servers. Configure the hostname, IP address and routing on three routers. Click the following link to learn more about configuring hostnames, IP addresses and Enhanced Interior Gateway Routing Protocol (EIGRP) in routers.
Click the following link to know where to place an Extended Access Control List (ACL). In this lab, the router near to the source network is Router01, and we have to configure Extended Access Control Lists (ACL) in Router01.
How to create Extended Access Control List (ACL) using "access-list" IOS command
To create a Extended Access Control Lists (ACL), to deny Workstation03 (IP address - 172.16.0.12/16) from 172.16.0.0/16 network, from accessing the Web Server (IP address - 172.20.0.5/16) at 172.20.0.0/16 network, we use the "access-list" IOS command from the global configuration mode of Router01 (which is near to the source) , as shown below.
Router01>enable Router01#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router01(config)#access-list 105 deny tcp host 172.16.0.12 host 172.20.0.5 eq 80 Router01(config)#access-list 105 permit ip any any Router01(config)#exit Router01#
Remember, there is an implicit "deny any" at the end of every Access Control Lists (ACL). If there is no "access-list 105 permit ip any any" statement at the end, above Extended Access Control List (ACL) may filter out all traffic. The "access-list 105 permit ip any any" permits any other IP traffic, if there is no matching deny in previous statements. Above Extended Access Control List (ACL) effectively allow all the traffic except the HTTP traffic from 172.16.0.12/16 to 172.20.0.5/16.
If you want to remove the Access Control List (ACL), use the "no" form of the command. You cannot delete a specific entry in an Access Control List (ACL). You can only delete the entire Access Control List (ACL), as shown below.
Router01(config)#no access-list 105
How to configure Extended Access Control Lists (ACL) to an interface using "access-group" command
The "access-group" command can be used to apply the access list to an interface. The syntax for "access-group" IOS command is given below.
Router(config)# interface interface_no
Router01(config-if)#ip access-group <access_list_number> <in/out>
The "in/out" keyword of the command is used to specify the direction in which the traffic is filtered.
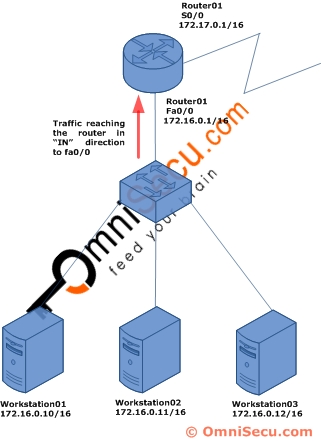
The "in" keyword is used to specify that the traffic should be filtered when it arrive the router via an interface. Following diagram explains the "in" keyword. Here the traffic will be filtered as it arrives the router.
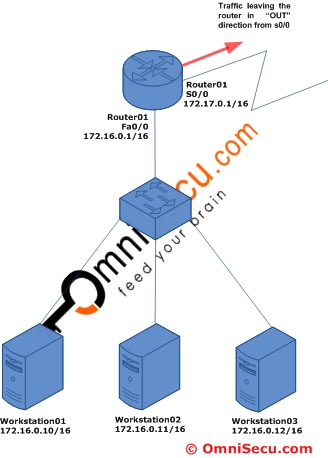
The "out" keyword is used to specify that the traffic should be filtered as it leaves the router via an interface. Following diagram explains the "out" keyword. Here the traffic will be filtered as it leaves the router.
Extended Access Control Lists (ACLs) must be applied close to the source network. Here the interface close to the traffic source is fa0/0 in Router01. Following IOS commands apply the Extended Access Control List (Access Control List No. 105) to the interface fa0/0 (Router01) in "in" direction.
Router01>enable
Router01#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router01(config)#interface fa0/0 Router01(config-if)#ip access-group 105 in Router01(config-if)#exit Router01(config)#exit Router01#
If you want to remove the Access Control List (ACL) from the above interface, use the "no" form of the command as shown below.
Router01(config-if)#no ip access-group 105 in