Why FTP is not secure
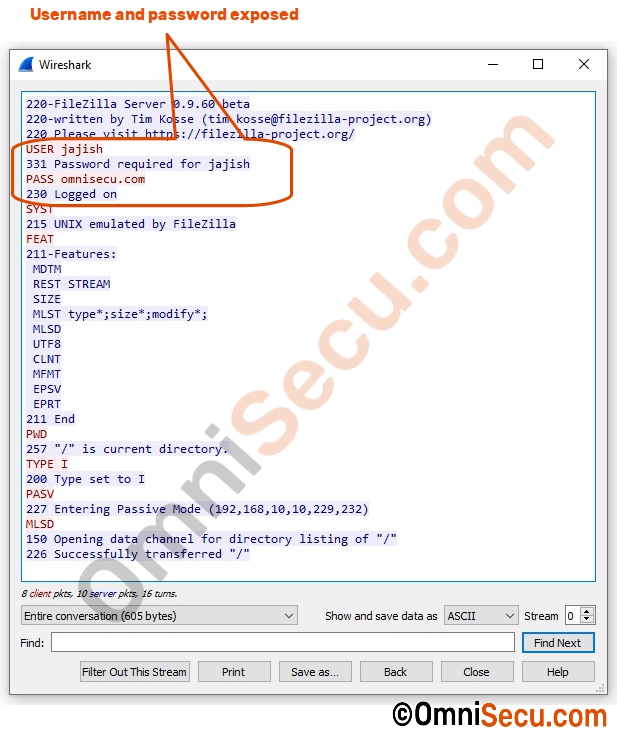
Similar to TELNET, FTP (File Transfer Protocol) was also not built to be secure. FTP (File Transfer Protocol) and TELNET were designed for networks of 1960s, 1970s and 1980s. During those periods, the computer networks were considered safe. FTP is considered as insecure protocol because it transfers user authentication data (username and password) and file data as plain-text (not encrypted) over the network. Because of this, FTP (File Transfer Protocol) is vulnerable to password sniffing, data spoofing, and other network attacks.

FTP (File Transfer Protocol) traffic between an FTP client and FTP server is not encrypted, unless VPN, or secure alternatives of FTP are used.
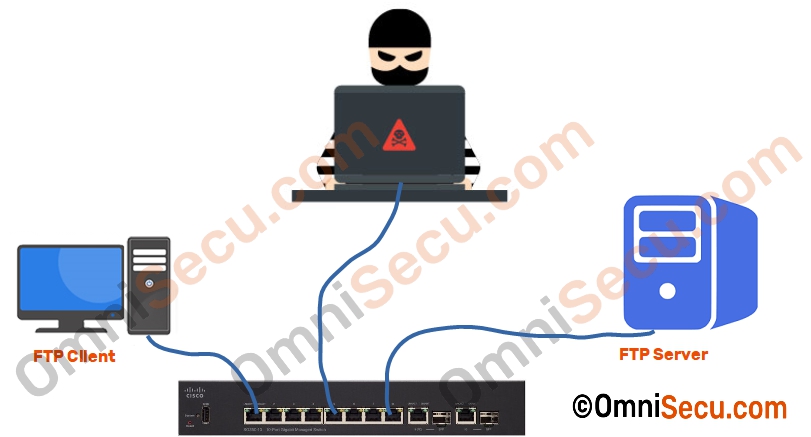
Secure alternatives of FTP (File Transfer Protocol) are FTPS (File Transfer Protocol Secure) and SFTP (Secure File Transfer Protocol). FTPS is an extension of FTP, which provides more security by using SSL/TLS features, but SFTP is an extension of SSH (SecureShell), which is a widely used secure network protocol.
Following image is a screenshot of Wireshark network traffic capture, which shows plain-text FTP (File Transfer Protocol) is highly insecure and dangerous.