What is NAT-Traversal (Network Address Translation - Traversal)
IPSec does not work if we have a NAT Device between two IPSec peers, performing Port Address Translation. It is not possible for the IPSec ESP packets to traverse (Travel across or pass over) across a NAT Device performing PAT.
Before proceeding, you need to know what is Network Address Translation (NAT) and what is Port Address Translation (PAT).
In Port Address Translation (PAT), the NAT Device changes the source Port Number (TCP or UDP) with another port number.To perform Port Address Translation (PAT), a NAT device must be able to open TCP/UDP header and find Source TCP/UDP Port Number. The TCP and UDP Port Numbers are not visible for a NAT device performing PAT between IPSec Peers, because TCP/UDP headers are encrypted and encapsulated with ESP header.
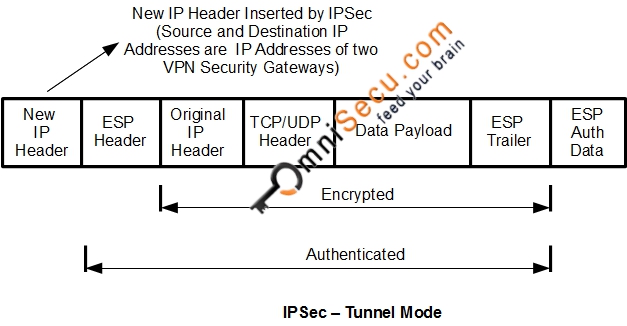
When IPSec is used to secure IPv4 traffic, original TCP/UDP Port Numbers are kept encrypted and encapsulated using ESP. Following image shows how IPSec encapsulates IPv4 datagram. For more details visit IPSec VPN Modes - Tunnel Mode and Transport Mode.
Following image shows a Wireshark capture of ESP encapsulated IPSec packet.
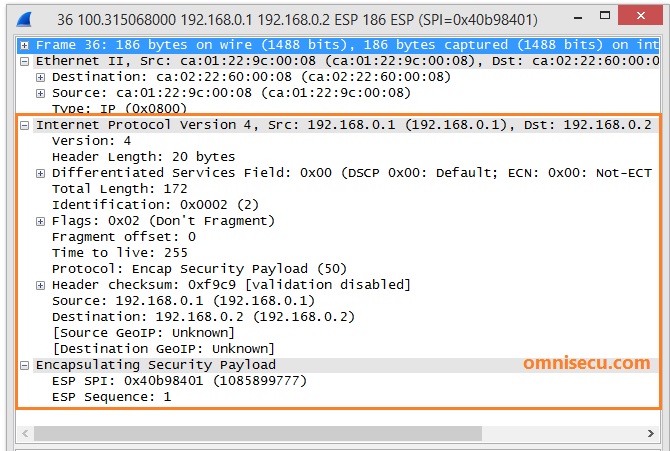
Note that TCP/UDP headers are not visible. TCP/UDP headers are kept encrypted as ESP data payload.
NAT Traversal (NAT-T) technology is used in IPSec to overcome above mentioned problem.
NAT Traversal (NAT-T) technology can detect whether both IPSec peers support NAT-T. NAT Traversal (NAT-T) technology can also detect NAT devices between IPSec Peers. ISAKMP Main Mode messages one and two are used to detect whether both IPSec peers support NAT-T. If both IPSec peers support NAT-T, NAT Devices are detected in ISAKMP Main Mode messages three and four.f
Once a NAT PAT device is detected between IPSec Peers, NAT-T encapsulates ESP packets inside an unencrypted UDP header with both Source and Destination ports as 4500. Now the NAT PAT devices have a UDP header and port number to play with and PAT happens as usual.